The service asset and configuration management process (SACM) is an important process in the ITIL Service Transition stage of the ITIL service lifecycle. Online ITIL training gives detailed explanations on the role of SACM in the ITIL lifecycle. In this article, we will revisit the SACM process and then we will discuss key knowledge which is also included in ITIL foundation exam questions by looking at the five process activities of the SACM process as a whole.
Revisiting SACM and its goals and objectives
Every service of an IT service provider is made up of components that contribute to the overall working of it. Let’s say for a messaging service, individual components that contribute are servers, software, networks, admins who run the show, and anything and everything else that chips in. SACM deals with these individual components, their attributes, and their relationships. Its omniscient presence through the service lifecycle makes it one of the most important processes in ITIL, and potentially the very first to be implemented.
Let’s revisit the goals of the SACM process before we focus on the five process activities. The first goal is to support the control objectives and the customer and business requirements. The second goal is to support an efficient and effective IT service management process. The third goal is to minimize the number of quality and compliance issues. And finally, the last goal is to optimize service assets, IT configuration, capabilities, and resources. The objectives of SACM is defining and controlling components of services and infrastructure. It also aims to maintain accurate configuration information on historical, current and planned states of services and infrastructure.
Now that we have context, we can discuss the five process steps of SACM.
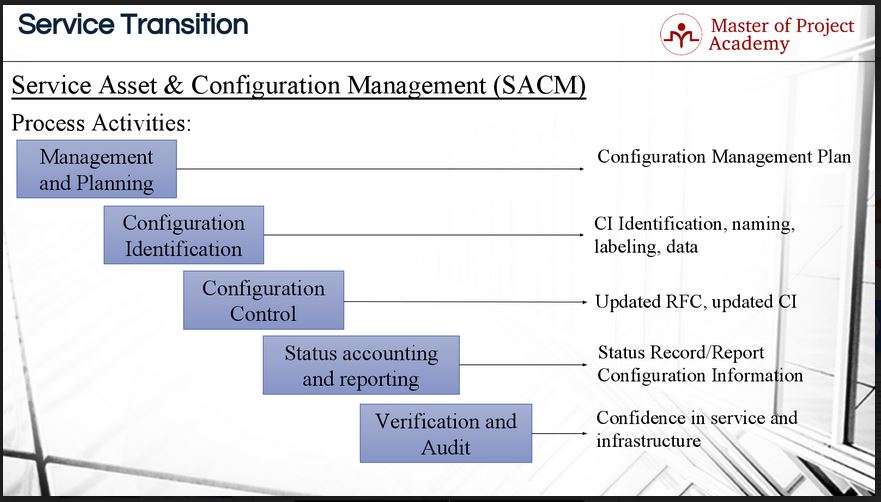
SACM: Management and Planning
The first activity is Management and Planning. IT service providers have several assets. Services, applications, tools, components etc. There must be a logical and structured versioning and release structure for configuration items in an IT service provider to eliminate confusion. The methods for doing versioning, building releases, establishing configuration baselines etc. must be done in a controlled manner. The methods for these activities are planned and documented in the SACM configuration management plan.
First, we need to plan on what we are going to consider a configuration item. It might so happen that a particular company wants to label individual components of a server as a configuration item. Another company on the other side of the spectrum might decide to call a cluster of servers a configuration item. Each IT service provider must decide which level of labeling configuration items will work best for them. A general practice across the service industry is to name a server as a CI, a router as a CI and sometimes, a monitor as a CI as well. Individual components that make up the CI are not managed individually and this must be taken into account.
SACM: Configuration Identification
The second activity is of SACM is Configuration Identification. After creating the configuration management plan, each configuration item of the IT service provider is named, labeled and the proper versioning of the configuration item is done. This will be of tremendous help if the configuration items must be reviewed at a later stage. Proper identification of configuration items sounds like a small action, but it can be of immense value later on in the SACM process. If the configuration items and their versions are not properly labeled it will be impossible to revert back to a configuration baseline state if a new version is deployed unsuccessfully.

SACM: Configuration Control
Then in the third activity of SACM, Configuration Control, changes to the configuration items are managed and changes are done in a controlled manner to each configuration item. There can be new requirements coming from the business for existing services, or a problem might be fixed in an existing service. These all require changes to the configuration details to the configuration as well. For instance, each change, version or release of the service must be updated as planned and described in configuration management plan.
SACM: Status accounting and reporting
The fourth activity of SACM is status accounting and reporting. At this step, details and information about the configuration items are recorded and reported periodically. Reporting on the status of the SACM process activities will give the IT service provider a clear view of how their service assets and configuration items are serving the objectives of the business. Also, the service provider can discover which assets and configuration items should be kept as is, changed or removed from the definitive media library. The regularity at which status reports on SACM activities must be compiled and delivered should be agreed upon during service level negotiations. This will ensure that all stakeholders will have a firm view of the SACM process within agreed upon timelines.
SACM: Verification and audit
The fifth and the last activity of SACM is verification and audit. After updating a service or changing a configuration item of an IT service provider, there can be impacts on other parts of the service management. For instance, after update on an existing service, if another service interacting with the updated service will have an interaction or compliance problem, this will affect the service delivery to the customer. Therefore, upon updates, changes or implementations at an IT Service provider, verification, and auditing takes place to assure the updates have been implemented successfully and did not have any impact for other configuration items.
These five process activities support the service asset and configuration management process. Without these five steps, the service asset and configuration management process cannot be successfully implemented. An IT service provider needs to have knowledge of all the configuration items that forms part of the IT infrastructure and these configuration items must be clearly identified and labeled. Any changes to these configuration items must be strictly controlled to ensure that no service disruptions take place. The status of the service assets and configuration items must be reported on regularly to all stakeholders. Regular reports will help to highlight any problems of improvements that need to be done. The final step, verification, and auditing is a crucial step to check whether all updates have been successfully deployed and that no other assets or configuration items have been affected downstream.
