We can easily say that Ethical Hacking is a confusing concept. Many people don’t understand what is Ethical Hacking and what Ethical Hacker is doing. Is Ethical Hacking a real job? Why a company is willing to pay a high amount for ethical hacking? Why people are getting Ethical Hacker trainings? Let’s explain what ethical hacking is!
First, let’s start with the history of Ethical Hacking. In the last 10 years, thousands of organizations have been hacked and lost millions of dollars, their reputations, and their customers. They have also faced legal issues because they were not able to secure their customers’ information which was stolen. The remarkable point here is that some of those organizations, like Sony, Yahoo, RSA, are big organizations. And they are spending a great amount on security in order not to get hacked; so that their information wouldn’t get stolen. That’s why they choose Ethical Hacking and decide to hire a hacker who tries to hack into their system and tells how he was able to hack them. Ethical Hacking serves to see what kind of weaknesses the company’s system has.
Ethical hacking professionals are getting hired by companies to hack their systems and to report back with the weaknesses. They help the company to learn which precautions they can take.
So ethical hacking is a valuable skill these days, that’s why there are several cyber security certifications and also many cyber security courses to get those certificates.
What are the phases of Ethical Hacking?
Ethical Hacking simulates what is done by malicious hacking to hack company. Ethical Hacking consist of 5 different phases as explained in CISSP certification training:
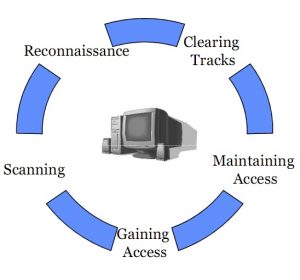
Phase 1: Reconnaissance
During this phase, Ethical Hackers gather information about their victim. Mainly passive information, which is available on public records, websites, and social media. They gather information such as emails, contact information, hobbies, friends, activities, etc.
During the fist phase, Ethical Hackers can collect technical information as well, like the victim’s IP, if the victim is a website. Ethical Hacker can get the registration information, the contact person’s email and phone number. All those information are very easy to get from the internet. Ethical Hacker can also get some confidential information like employment history or background information.

Phase 2: Scanning
During second phases, Ethical Hackers will also collect information about their victim. But this time active information such as open ports on the victim’s computer, services, and applications, what operating system the victim is using and the network topology if the target is a network. Using that information, Ethical Hackers will do some advanced search to know which service, port, application or operating system is vulnerable and can be used to hack the system. And how the Ethical Hacker can hack that system using those vulnerabilities.
Phase 3: Gaining Access
From the first and the second phases, Ethical Hacker will have a clear idea about the victim systems and the vulnerabilities that he can use to hack the system and to get access to the information. So they will start using them to gain access to the system. The system could be a personal computer, a computer network, a website or a wireless network.
Phase 4 of Ethical Hacking: Maintaining Access
After the third phase, the Ethical Hacker who is now able to hack the system needs to maintain his access so he doesn’t have to repeat all those steps in the future. This can be done easily by combining himself to any system process and by doing that, the system owner will not be able to get rid of the Ethical hacker. So the hacker will be always spying on this system.

Phase 5 of Ethical Hacking: Covering tracks
Since hacking is a crime, any malicious hacker after hacking any system will try to delete all the logs and any evidence that may be used against him. Ethical Hacker needs to follow the same steps to check if the logging system of the company is effective and capture logs properly or can be manipulated be any malicious hacker.
Finally, after all those phases, the Ethical Hacker needs to write a report to explain what he did in each phase, what was his findings and which proper countermeasures he recommends.
Ethical Hacking is a new type of the security jobs, that has high demand in the market today. Ethical Hacker gets well paid for doing that, especially if they are qualified and hold some professional certificate. If you are willing to get a Certified Ethical Hacker (CEH) Certificate, wait no more to enroll in a CEH certification training. If you want to learn more about CEH renewal you can read the article by clicking on the link.
You can enroll in free CISSP training to learn more about CISSP certification.
Author Biography:

Mohamed Atef, Information Security Expert with more than 20 years of experience that entails Information Security, Penetration testing and Information Security Management (CISSP Certified), Data Centre, System Administration, MS SharePoint Administration, and Network Infrastructure Management. Credited with managing several projects related to Information Security, DRP, and BCP, SharePoint Implementation, ISO 27001, Infrastructure and Data Centre implementation. Published two books. Qualifications include MBA in Information Technology Management supplemented by various professional certifications like CISSP, ITIL, MS SharePoint, CCNP, CEH.

